OverTheWire: Natas
Natas Natas teaches the basics of serverside web-security. Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There i...
Natas Natas teaches the basics of serverside web-security. Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There i...
Bandit The Bandit wargame is aimed at absolute beginners. It will teach the basics needed to be able to play other wargames. It focuses on basic shell commands like Tools: ls, cd, cat, file, du, ...

Every hacker, sysadmin, gamer, and everyday user relies on something critical to make their computer run: the Operating System (OS). Think of it like the brain behind your machine, handling everyth...

In the digital age, productivity suites are the bread and butter of most workplaces, classrooms, and even hacker dens. Whether you’re writing reports, crunching numbers, or saving digital notes fro...

Let’s face it, if you’re diving into cybersecurity without understanding how devices actually talk to each other, you’re flying blind. Networks are the battlefield of modern cyber warfare, and if y...

Let’s be honest, whether you’re on Windows, Linux, or macOS, tech can break. Systems slow down, apps freeze, things stop working and suddenly you’re the person everyone’s looking at like, “Can you ...
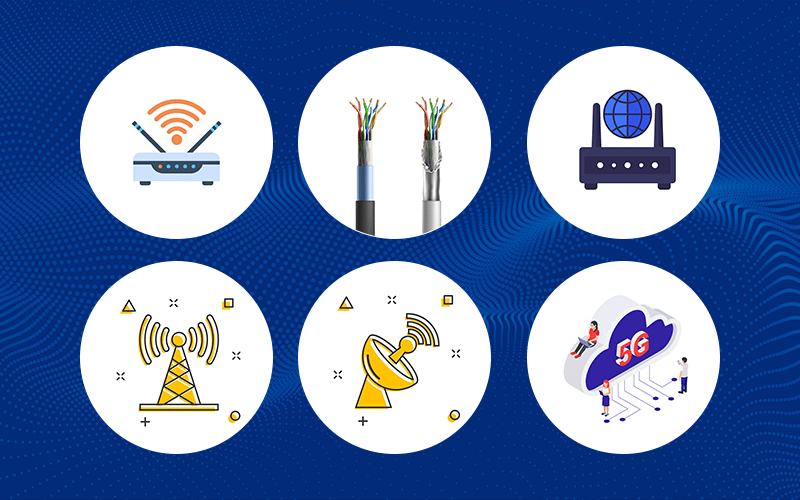
If you’re just getting started in cybersecurity, one of the first things to understand is how devices connect to each other. Whether it’s your phone syncing with earbuds or a laptop connecting to t...
Solutions As you can see the title of the challenge, we will notice that this challenge is about SSTI, so let try ${7*'7'}} in any input form. But first, we need to register account. In Personal...
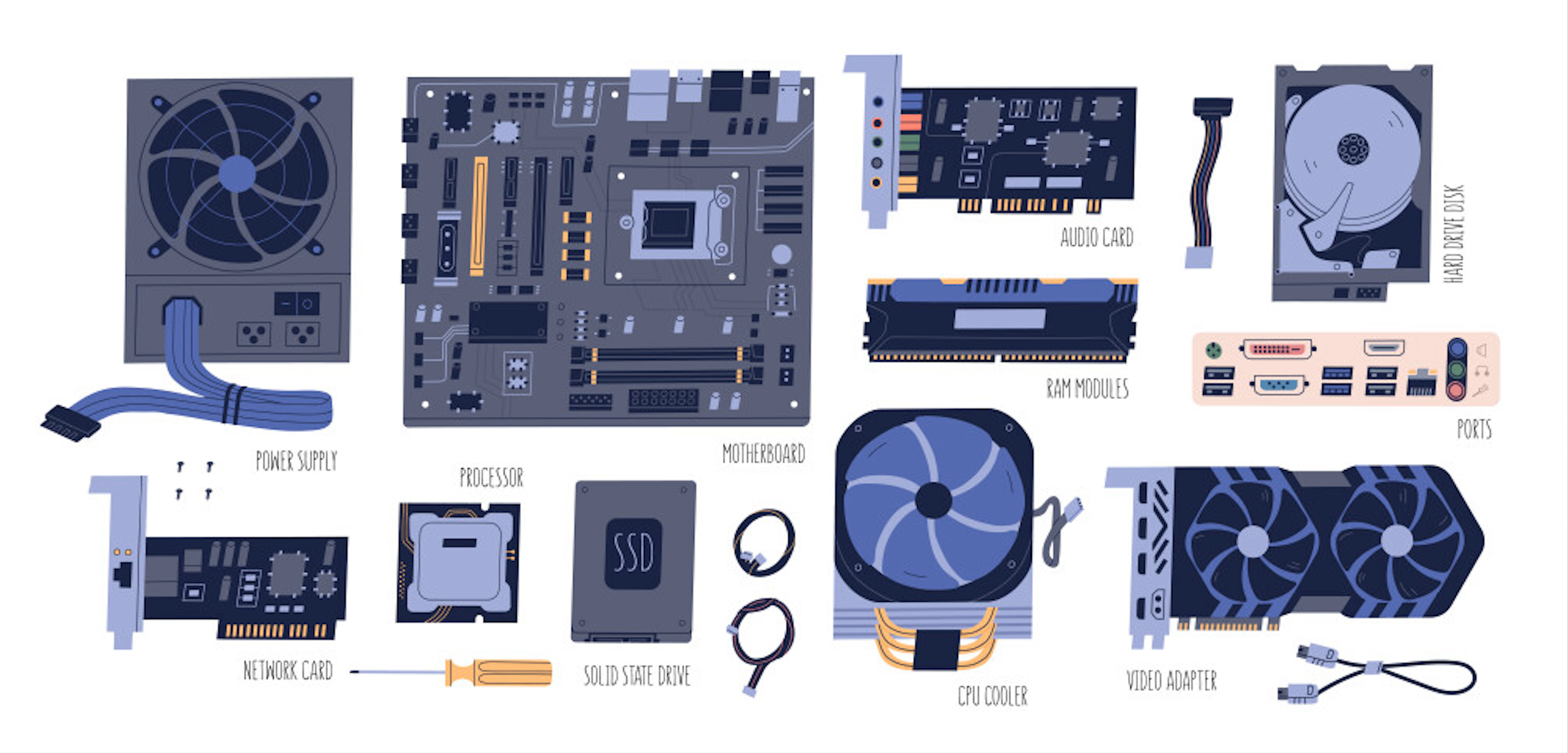
If you’re diving into cybersecurity, whether you dream of becoming a hacker, defender, or forensics wizard you need to understand the machine you’re working with. Before you start popping shells o...

So you have decided to dive into cybersecurity? Maybe you have heard about ethical hacking, Capture The Flag (CTF) challenges, or just want to break into tech in a fun and hands-on way. Good news:...