Litter
CHALLENGE DESCRIPTION
Khalid has just logged onto a host that he and his team use as a testing host for many different purposes. It’s off their corporate network but has access to lots of resources on the network. The host is used as a dumping ground for a lot of people at the company, but it’s very useful, so no one has raised any issues. Little does Khalid know; the machine has been compromised and company information that should not have been on there has now been stolen – it’s up to you to figure out what has happened and what data has been taken.
SOLUTION
At a glance, what protocol seems to be suspect in this attack?
At a glance, we can see lots of packets with DNS protocol.
Answer
DNSThere seems to be a lot of traffic between our host and another, what is the IP address of the suspect host?
Go to Statistics > IPv4 > All addresses > Sort Count colunm.
Answer
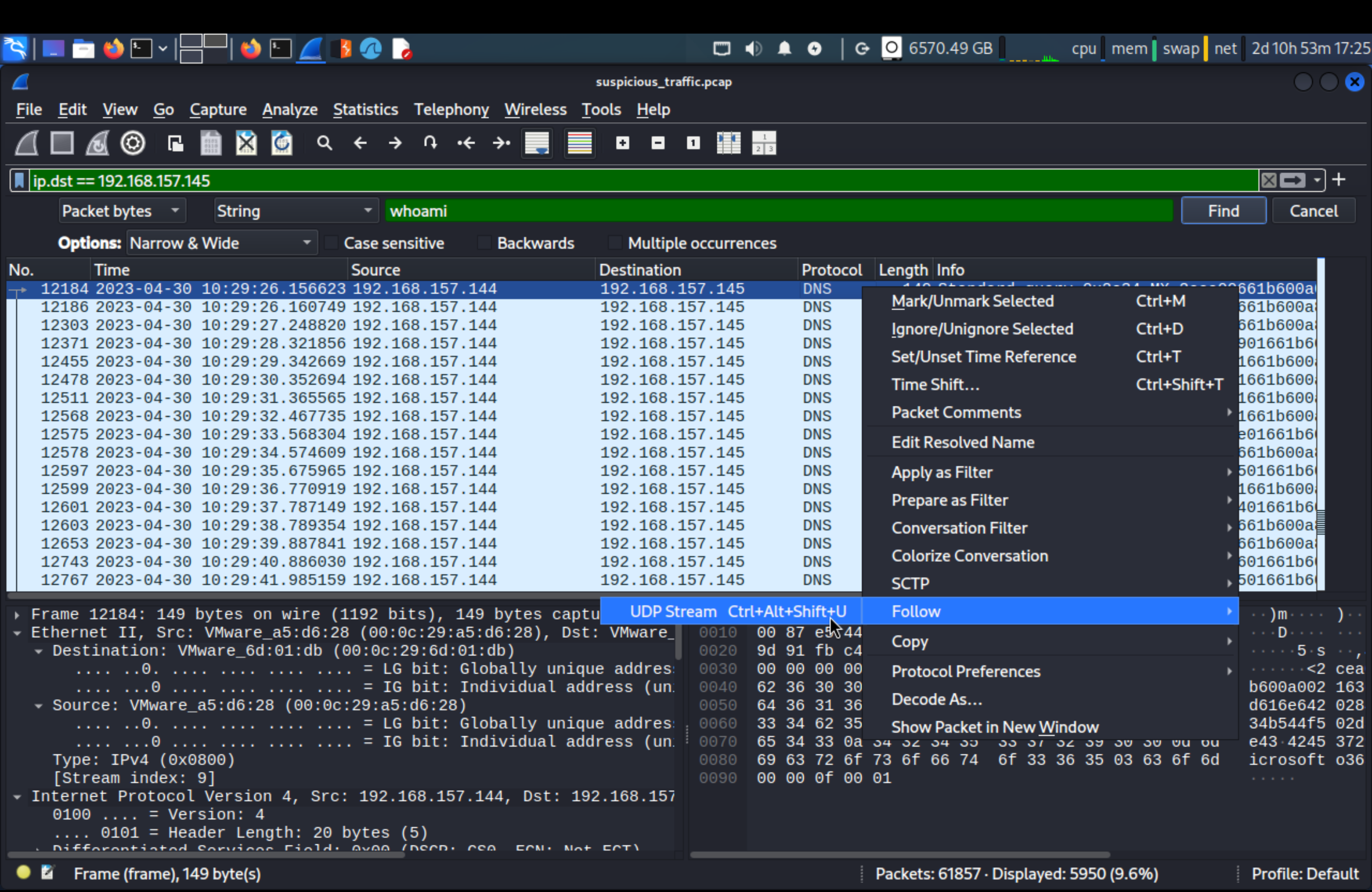
192.168.157.145What is the first command the attacker sends to the client?
We totally can guess that, when attackers have access to target’s machine, the first thing the attackers do is checking the current user that is logged in.
Filter ip.dst == 192.168.157.145 and follow first packet, copy all of the content from that packet and paste in CyberChef > From Hex.
Answer
whoamiWhat is the version of the DNS tunneling tool the attacker is using?
We can get the flag from the above decrypted hex.
Or we can download tool to help us analyze easier: DNScat
Answer
0.07The attackers attempts to rename the tool they accidentally left on the clients host. What do they name it to?
The target’s machine is WindowOS, so they use cmd or powershell, so ren for rename.
1
grep -ri 'ren ' dnscat_dump.txt
Answer
win_installer.exeThe attacker attempts to enumerate the users cloud storage. How many files do they locate in their cloud storage directory?
Cloud storage means OneDrive.
Answer
0What is the full location of the PII file that was stolen?
Read the log slowly, and carefully =))
Answer
C:\Users\test\Documents\client data optimisation\user details.csvExactly how many customer PII records were stolen?
Columns in database
1
ID,job,company,ssn,residence,current_location,blood_group,website,username,name,sex,address,mail,birthdate
scroll down to the end of the log and we can see the ID of the last user. Because ID starts from 0, so we need to add 1 more in the flag.