Event-Viewing
Event-Viewing
CHALLENGE DESCRIPTION
SOLUTION
First, we need to convert evtx to xml to analyze
1
2
3
pip install python-evtx
source myenv/bin/activate
python3 evtx_dump.py some.evtx > some.xml
We read the hint and do research about EventID 
Now we know some ID number of events, so filter it with grep. A25 flag can list 25 lines after each match.
1
cat some.xml | grep -A25 "1033</EventID>"
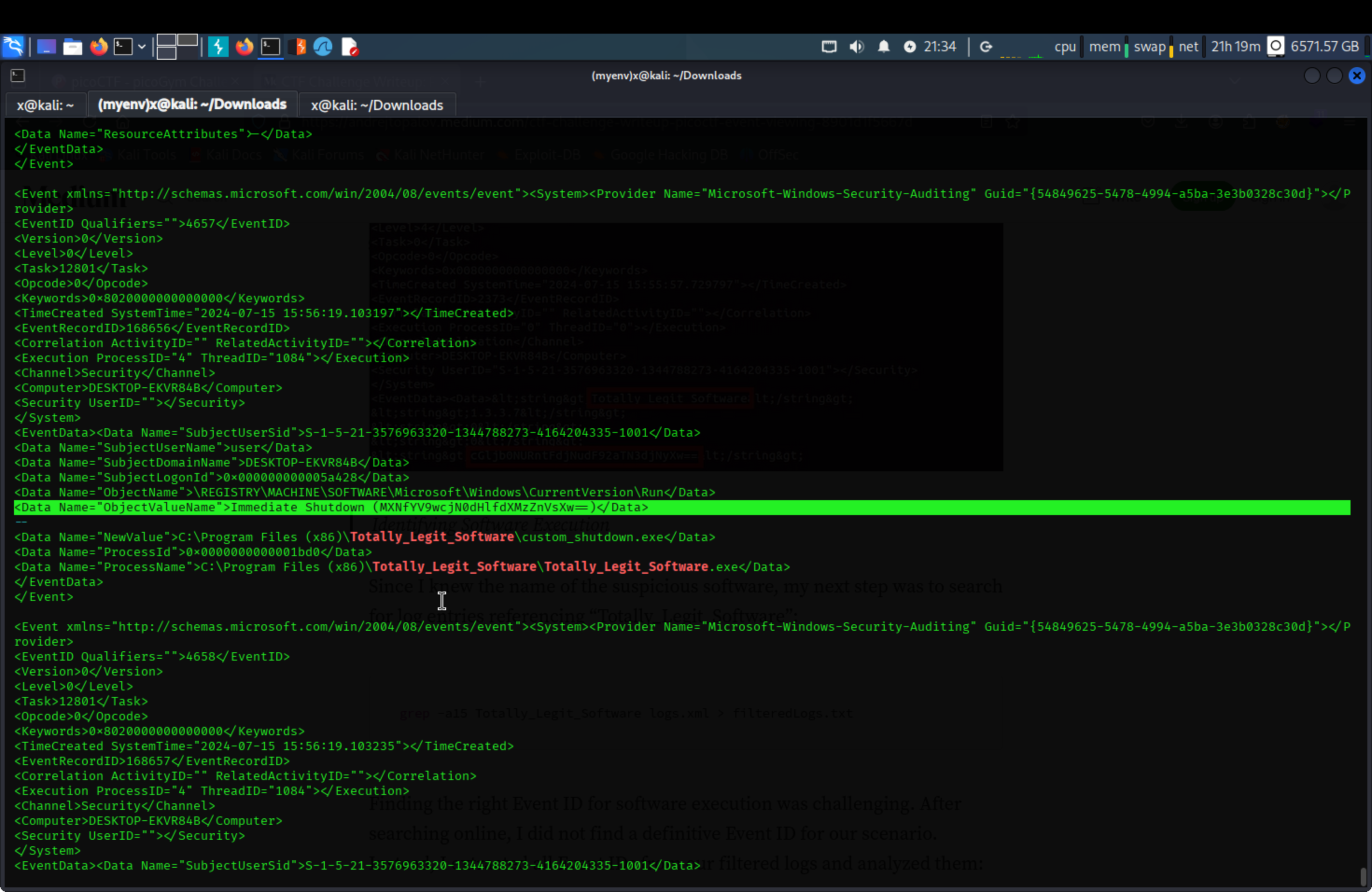
We get the first part of the flag, and the malicious software’s name.
1
2
cat some.xml | grep -A25 "Totally_Legit_Software"
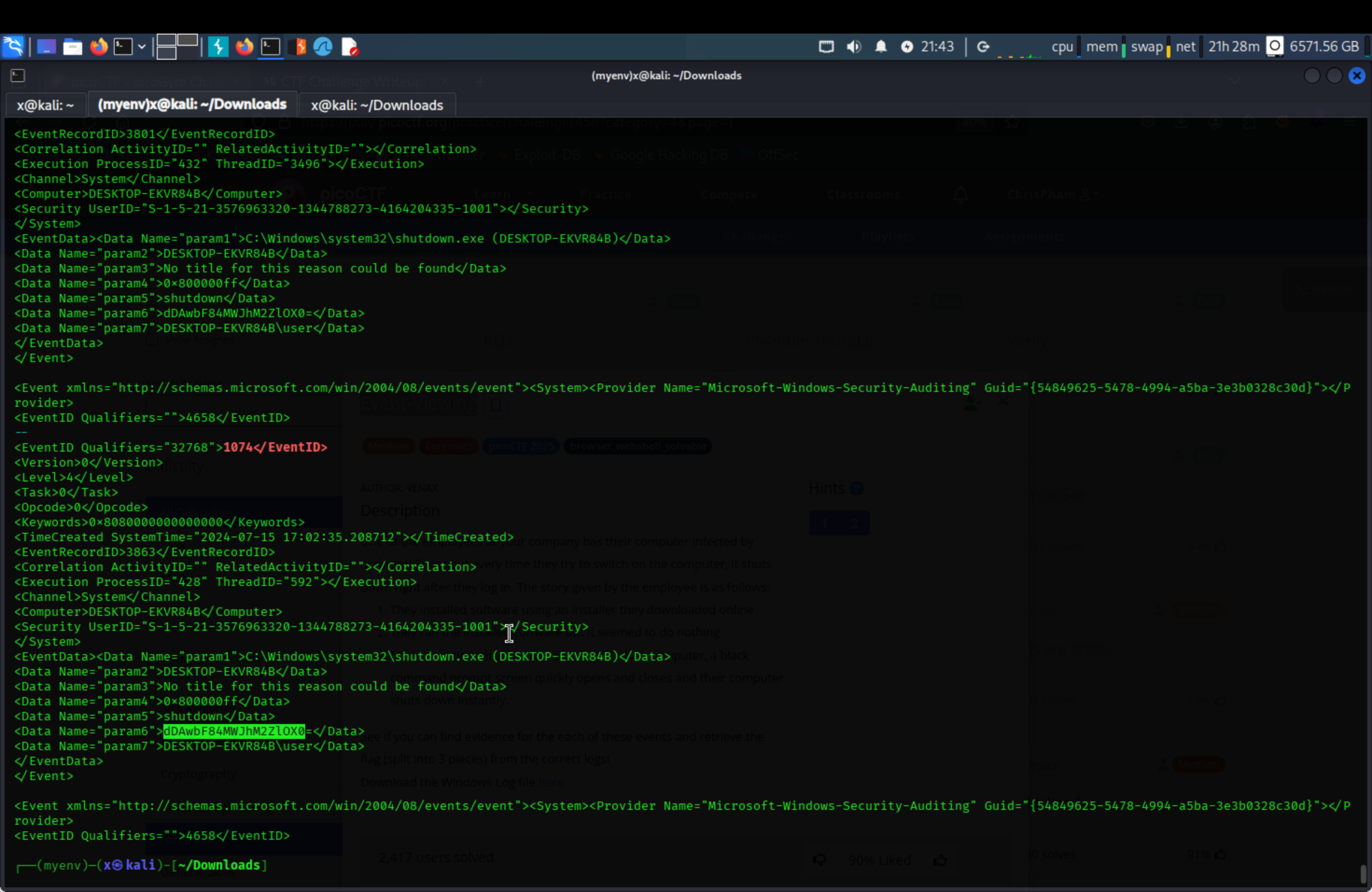
We got the second part of the flag, now filter the shut down eventid.
1
2
cat some.xml | grep -A25 "1074</EventID>"