Connection Types And Their Functions
If you’re just getting started in cybersecurity, one of the first things to understand is how devices connect to each other. Whether it’s your phone syncing with earbuds or a laptop connecting to the internet, every connection can be a potential attack point.
This blog breaks down the most common connection types, what they do, and why they matter in cybersecurity. Let’s get into it.
Table of Contents:
Ethernet
 Ethernet is the classic wired connection that plugs into your computer or router using an Ethernet cable:
Ethernet is the classic wired connection that plugs into your computer or router using an Ethernet cable:
- Super stable and fast
- Great for gaming, streaming, or business networks
- Used in most corporate environments
Notes:
- Less vulnerable to wireless attacks like sniffing or spoofing
- But attackers can still plug into the network physically if ports aren’t secured
- Use network segmentation, port security, and monitoring to stay safe
Types of Networks
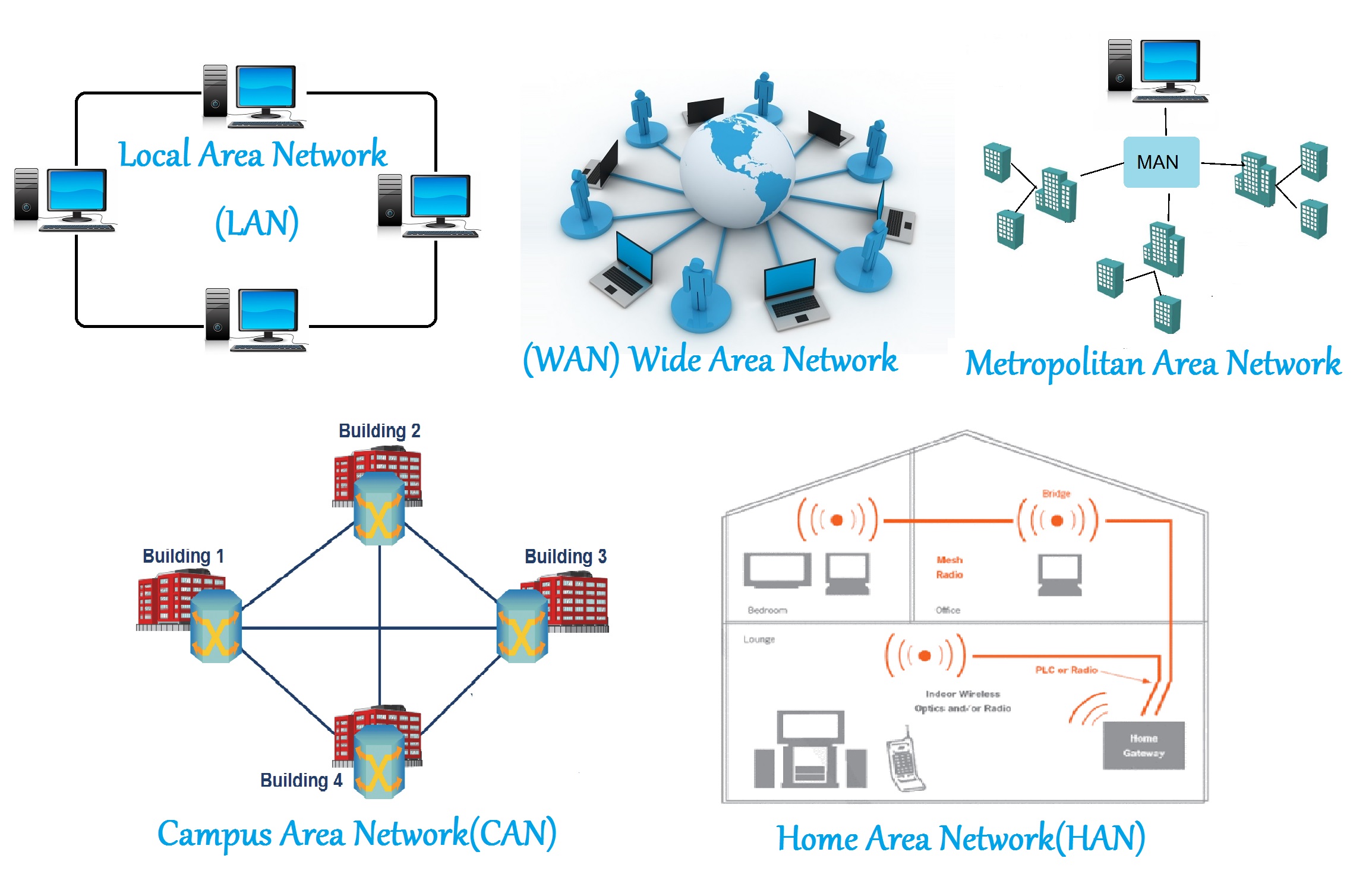 Different network types define how far your data can travel, each type determines how devices connect and communicate, and what infrastructure is involved:
Different network types define how far your data can travel, each type determines how devices connect and communicate, and what infrastructure is involved:
- LAN (Local Area Network): Home or office network
- WAN (Wide Area Network): Like the internet, large-scale connection across regions
- PAN (Personal Area Network): Your phone, smartwatch, earbuds
- MAN (Metropolitan Area Network): City wide networks
Notes:
- LANs are easier to manage and secure
- WANs are harder to secure and often targeted by attackers
- PANs can be exploited via Bluetooth/NFC vulnerabilities
- MANs may rely on public infrastructure = more risk
Wi-Fi
 Wireless connection used at home, cafes, airports, etc. Makes the internet portable:
Wireless connection used at home, cafes, airports, etc. Makes the internet portable:
- Connects devices to a router without cables
- Uses radio waves (2.4 GHz / 5 GHz / 6 GHz)
Notes:
- Weak Wi-Fi passwords and old protocols (WEP, WPA) = huge risk
- Always use WPA2/WPA3 encryption
- Avoid public Wi-Fi unless using a VPN
- Watch out for Evil Twin attacks (fake hotspots)
Bluetooth
 Wireless tech for short-distance communication, think headphones, speakers, smartwatches:
Wireless tech for short-distance communication, think headphones, speakers, smartwatches:
- Pairs devices over short distances
- Quick and convenient for file transfers and audio
Notes:
- Vulnerable to Bluejacking, Bluesnarfing, and Blueborne attacks
- Turn off Bluetooth when not in use
- Don’t accept random pairings or file transfers
Fiber-Optic
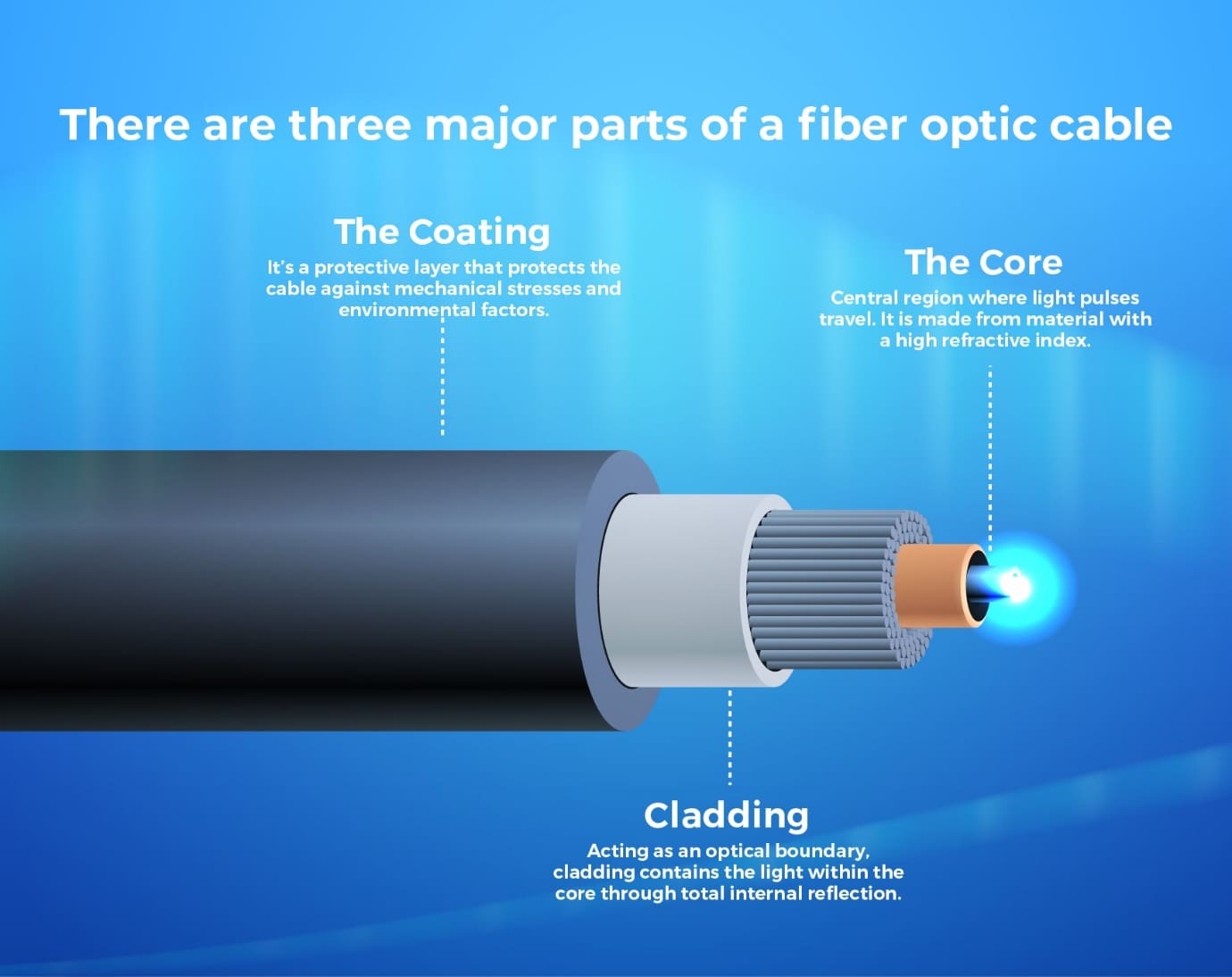 High-speed internet delivered through thin strands of glass using light signals:
High-speed internet delivered through thin strands of glass using light signals:
- Fast, secure, and immune to electromagnetic interference
- Used in data centers, ISPs, and high-demand networks
Notes:
- Difficult to tap without physically damaging the cable
- But still vulnerable at endpoints (routers, switches, devices)
- Encrypt data in transit even on fiber to stay protected
Cellular (4G/5G)
 Mobile data provided by your phone’s carrier:
Mobile data provided by your phone’s carrier:
- Lets phones and tablets access the internet wirelessly from anywhere
- 5G offers faster speeds and lower latency
Notes:
- Can be more secure than public Wi-Fi
- But can still be intercepted with fake cell towers
- Avoid using cellular for sensitive business activities without protection
NFC (Near Field Communication)
 A super short-range wireless connection used in tap-to-pay systems and quick device pairing:
A super short-range wireless connection used in tap-to-pay systems and quick device pairing:
- Requires devices to be within a few centimeters
- Super fast and convenient
Notes:
- Limited range = harder to hack remotely
- Still vulnerable to relay attacks, eavesdropping, or unauthorized scans
- Disable NFC when not using it
Infrared (IR)
Wireless tech that sends signals via infrared light:
- Mostly used in remotes and old mobile devices
- Very short range, line-of-sight required
Notes:
- Not widely used in modern hacking, but still can be exploited in air-gapped environments
- Limited use = limited risk, but don’t ignore it entirely if you’re in sensitive environments
Why This Stuff Matters in Cybersecurity
Every connection type you use opens a door. As a cybersecurity professional, your job is to know which doors are open, which are locked, and which are being picked.
Here’s what to focus on:
- Use strong encryption on all connections
- Disable what you’re not using
- Understand how attackers abuse public or wireless networks
- Always ask: “If I was an attacker, how would I exploit this connection?”
Final Thoughts
Your journey in cybersecurity starts with understanding the basic ways devices communicate. Once you know how connections work, you can better secure them, monitor them, and break into them.
Take Action:
- Check your Wi-Fi settings. Are you using WPA3?
- Go through your phone and disable unused connections (Bluetooth, NFC)
- Try packet-sniffing your Wi-Fi with Wireshark
Stay curious, stay safe, and remember every packet tells a story.
Happy Hacking!