Compromised
CHALLENGE DESCRIPTION
Our SOC team detected suspicious activity in Network Traffic, the machine has been compromised and company information that should not have been there has now been stolen – it’s up to you to figure out what has happened and what data has been taken.
SOLUTION
What is the IP address used for initial access?
Search for HTTP, we will see the first packet, copy value from IP source.
Answer
162.252.172.54What is the SHA256 hash of the malware?
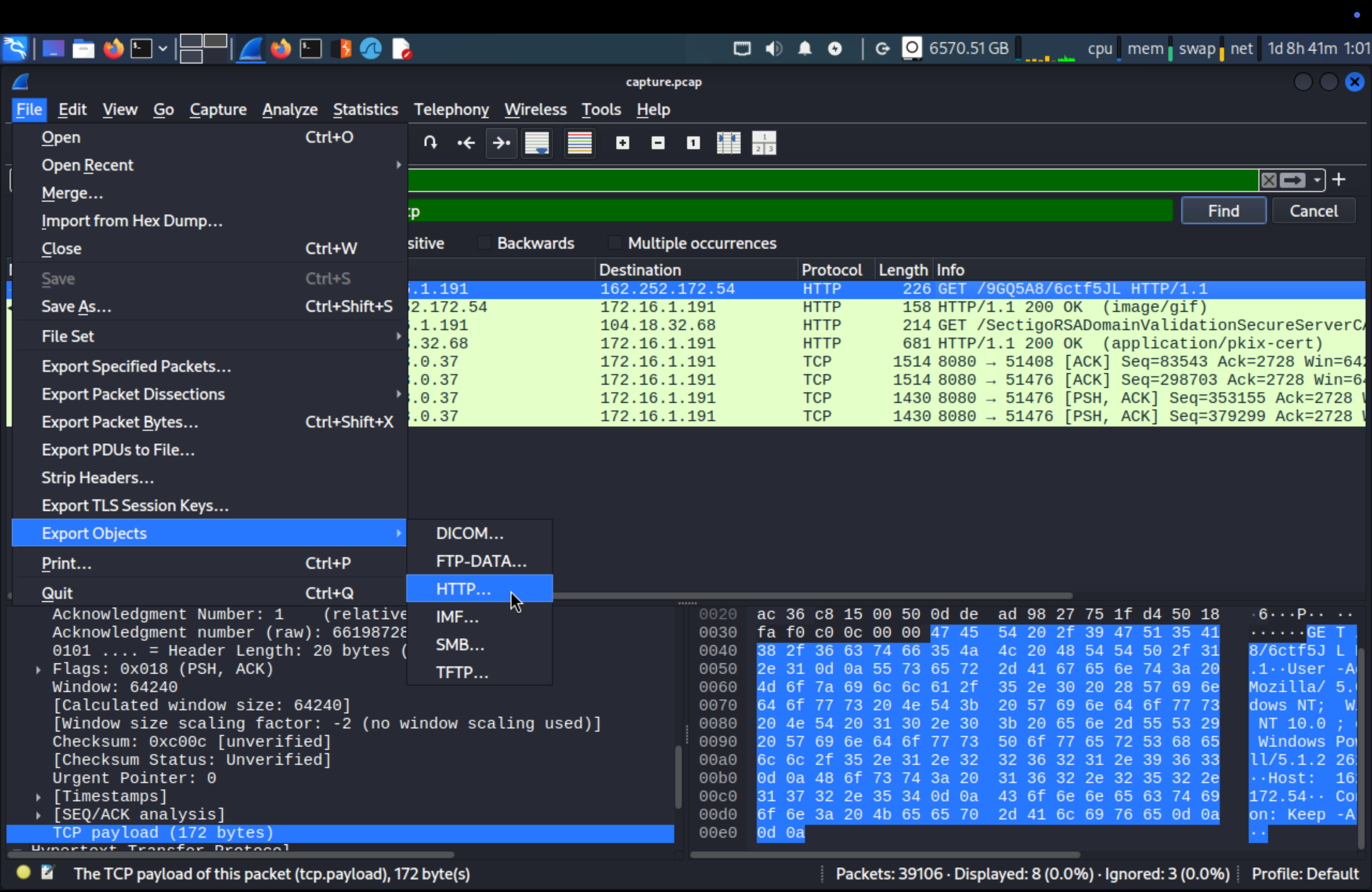
We need to export HTTP and download the file.
After downloading, we need to check its status by VirusTotal
Answer
9b8ffdc8ba2b2caa485cca56a82b2dcbd251f65fb30bc88f0ac3da6704e4d3c6What is the Family label of the malware?
Click on Relation tab on VirusTotal and search for parent
Answer
PikabotWhen was the malware first seen in the wild (UTC)?
Answer
2023-05-19 14:01:21The malware used HTTPS traffic with a self-signed certificate. What are the ports, from smallest to largest?
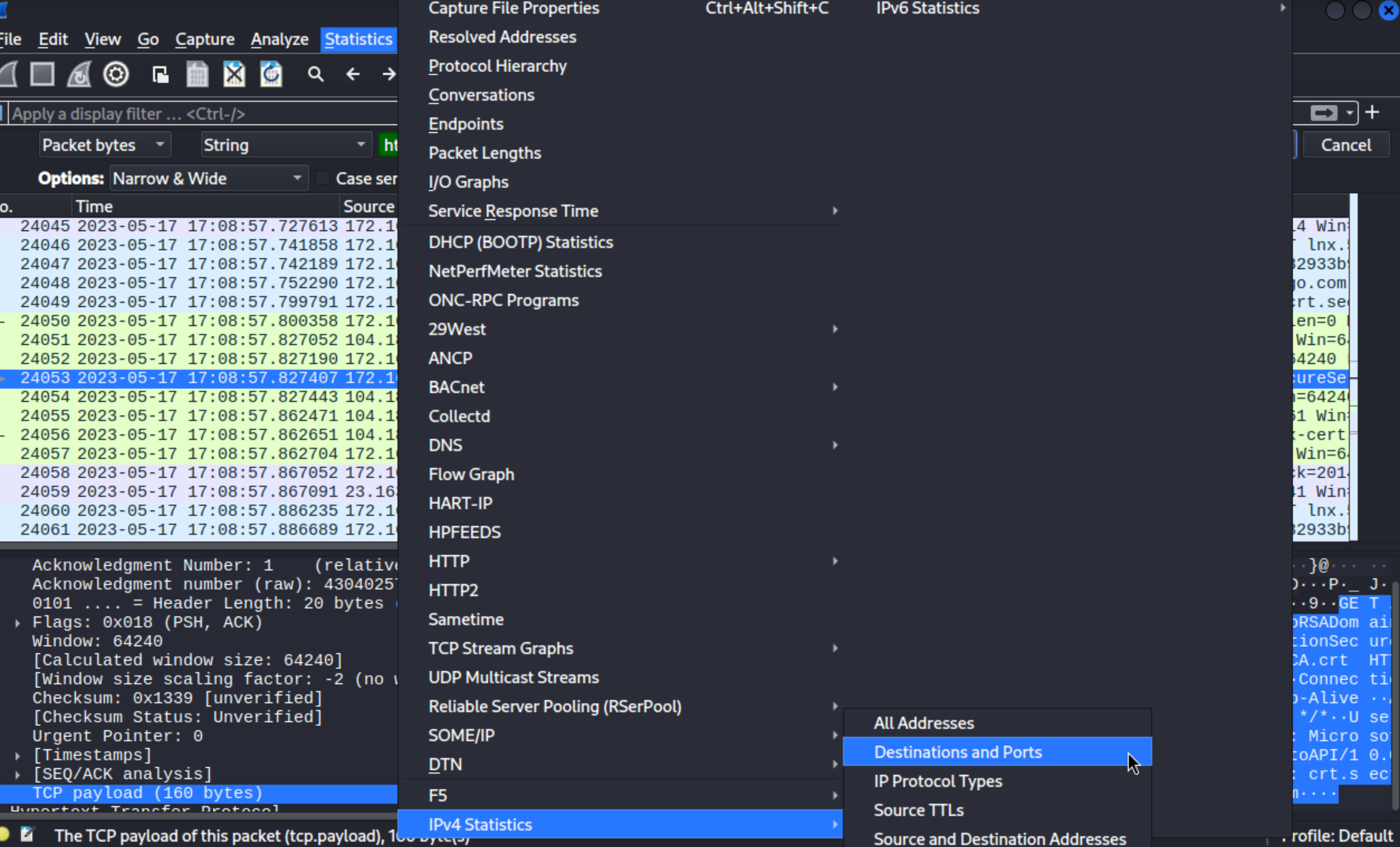
To analyze ports, we should go to Statistics > IPv4 > Destination and Ports
Filter TLS
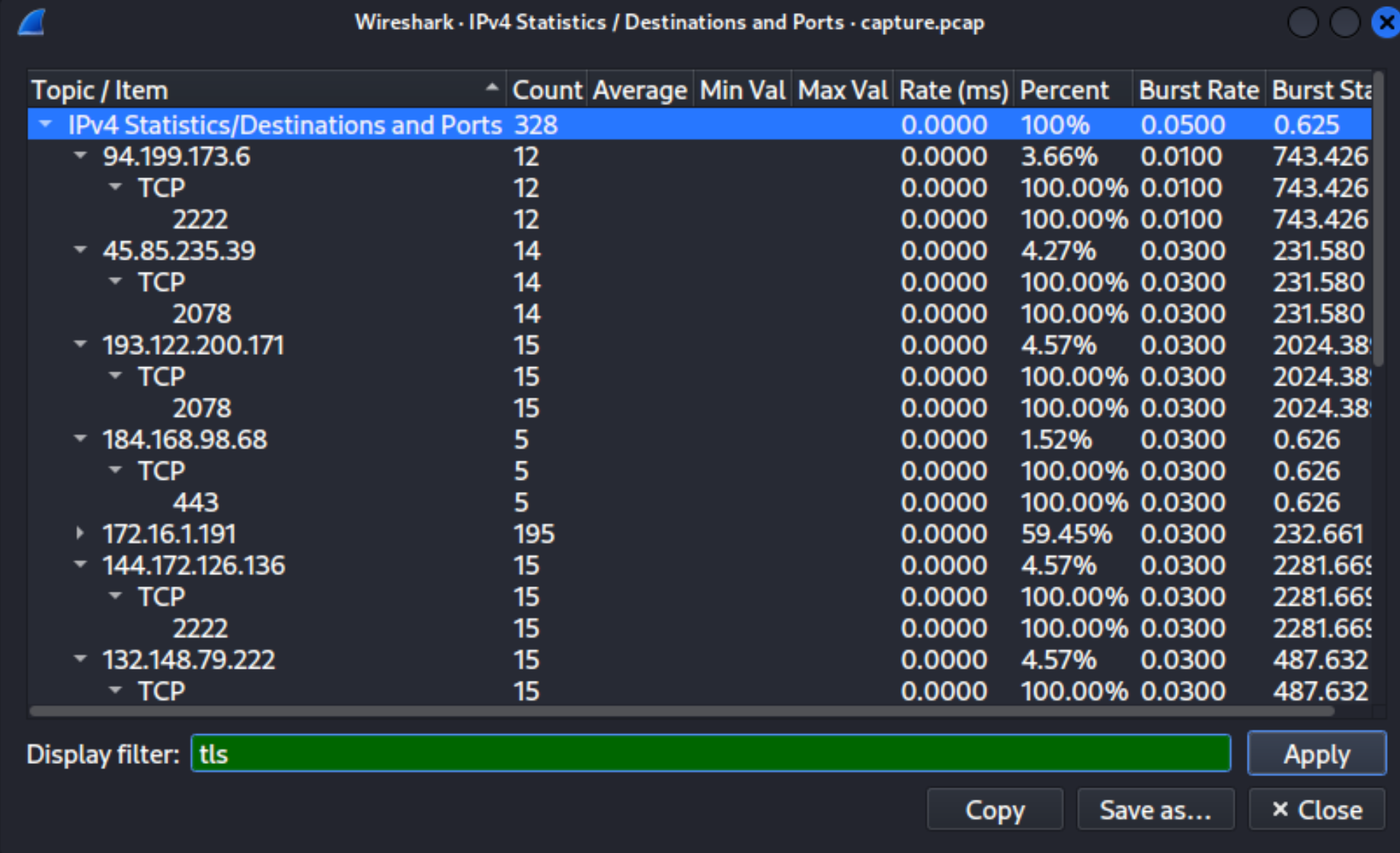
We will see some non-default ports there.
Answer
2078, 2222, 32999What is the id-at-localityName of the self-signed certificate associated with the first malicious IP?
1
tls.handshake.certificate
We will see Sever Key Exchange, analyze the first packet > Transport Layer Security > Handshake protocol > Certificates > Certificate > Issuer > id-at-localityName.
Answer
PyopneumopericardiumWhat is the notBefore time(UTC) for this self-signed certificate?
Transport Layer Security > Handshake protocol > Certificates > Certificate > validity > notBefore
Answer
2023-05-14 08:36:52 (UTC)What was the domain used for tunneling?
Search DNS and we will see the domain on the Info colunm.